One of the benefits of purchasing an Apple phone is that the updates tend to be highly optimized. Android operating system releases need to cover a broad spectrum of different phones and hardware. It is impossible for the Android update to work perfectly on each and every one of them. This means that one day you may have a phone which works exceedingly well, and the next it just performs sluggishly. You are not going to have to worry about that with an iOS update. The update would have been tested over and over again on the exact device that you are using. This means that there will be an improvement in your device. You do not have to sit around waiting for a fix in the vast majority of cases. Yes, Apple are guilty of pushing poor quality updates from time to time. Not everything can be tested perfectly. However, they tend to patch these bugs pretty quickly.
Friday, July 10, 2015
Why iOS software updates are better than android updates?
iOS, as you may well know, is the name of the operating system on mobile devices made by Apple i.e. the iPad and iPhone. It is also available on some versions of the iPod. On this page, we are going to take a little look at why iOS software updates are far superior to Android operating system updates, the competitor to Apple.
Apple produce the operating system that they use on their phone. Google produce Android, an open source operating system. Now, open source has plenty of benefits. Many phone manufacturers will play about with the code to make it work better for them. However, open source also has its downsides. Anybody can access open source code. This means that anybody, with the knowledge to do so at least, put together malicious software that you could accidentally include on your phone. In addition to this, the manufacturers who rewrite the operating system for their own purposes may play about with the code and break it, never to release a fix (the standard Google operating system will be tough to work with). So, in short, Apple coding is closed coding. This means that the only people who can view the code are those that work for Apple. This means that the security of iOS operating system updates tend to be slightly better and thus safer for you to use.
Now, many people will say that iOS nowadays tries to copy Android as much as possible. It does, to some extent. However, when Apple try to do something with their operating system, they make sure that they go above and beyond to ensure that the operating system boasts better features. Sure, features may take a while to come out for iOS, but you can be sure that they are going to be better than the Android equivalent in the vast majority of cases.
Recently some SSL vulnerabilities (Heart-bleed, Freak) were identified by security researchers, Apple did release the patched software updates after a few days but in case of android Google does not release any updates for Android versions prior to 4.4 -KitKat, Its a free pass for Hackers to steal your Credit card & personal informations, even if Google releases security updates, the company vendors (Samsung, HTC, LG) which makes the android phone must apply the Patch to the source code and push the update to the Phone, in most of the cases an Android user never get the latest updates or security updates, but Apple doesn’t rely on third party, it release the updates on time, an iPhone user is 99% secure than an Android user.
Apple launches two new “If it’s not an iPhone” ads
Today, Apple launched two new iPhone advertisements touting the device’s uniqueness and how much its customers love them. In the first ad, entitled Hardware & Software, Apple big-ups the way the iPhone’s hardware and software are both created by the same company.
In the second advertisement, entitled Love, Apple touts how 99% of iPhone customers love their devices. It then ends both advertisements with a similar tag line: If it’s not an iPhone, it’s not an iPhone.
Even though many devices have tried to copy Apple’s hardware or software efforts, due to the fact that Apple is one of the few that produces both, it’s able to have a leg up on Android OEMs when it comes to software and hardware synergy.
And it’s true, there simply is nothing like an iPhone. You may not like it, you may prefer something else, but there’s no denying that there’s nothing quite like the sum of all of its parts when it comes to the competition.
As someone who likes to try other phones, I can attest that many Android phones do a good job as far as smartphones go. But there’s just something about having both components designed by the same company that makes things mesh like no other.
Agree, or disagree? And what do you think about those new ads?
Wednesday, July 8, 2015
SwipeForMore lets you manage Cydia items with just a swipe
If you find the stock method of managing Cydia packages to be a bit cumbersome, then you’re not alone. Fortunately, saurik has opened up Cydia to third-party modifications, and for that we all are very thankful.
As expected, many new jailbreak tweaks specifically designed for Cydia are beginning to appear. One of the latest tweaks, entitled SwipeForMore, looks like one of the most compelling one thus far.
SwipeForMore allows you to swipe on a tweak in order to access install and uninstall options. It can save you time, because you don’t have to navigate into a tweak’s individual page in order to manage it.
SwipeForMore is an awesome tweak that will surely become a staple for many. Simply being able to swipe on a tweak to install, queue, or uninstall, is so much faster than the old way of managing packages.
Queuing, in particular, benefits from SwipeForMore. When you use queueing via SwipeForMore’s interface, the Confirm dialogue pops up, but then automatically disappears in order to accept your next command.
It’s really hard to appreciate how much this speeds up the workflow without seeing it in action, hence, you should definitely watch the video above to see SwipeForMore and other new Cydia-centric tweaks in action.
There are a couple of options in the Settings app for SwipeForMore. There’s a kill-switch for quickly disabling a tweak, and there’s a skip confirmation switch that allows you to skip the confirm dialogue for even faster installs.
It won’t be a tweak that you can use with every Cydia install since it doesn’t yet play nice for paid packages, but it can handle free packages and packages that have already been purchased like a champ.
What do you think about SwipeForMore. Drop us a line in the comments.
How to get Android-inspired cellular signal and Wi-Fi status bar icons
Today I bring to you a two awesome android wifi and cellular icone if you're a fan These icons are added to the status bar by means of a WinterBoard theme downloadable for free from Cydia. In this post, I’ll show you how you can add them to your iPhone.
To get these awesome looking status bar icons, open Cydia and search for Android Solid, which is a free download. Once you download it, you may need to reboot if you don’t already have WinterBoard.
One you enable the two themes, tap the back button and tap respring. Once you do, you should see the new Android L-styled Wi-Fi and cellular signal meters in your status bar.
Again, Android Solid is a free theme available right now on Cydia. Have you tried out this theme, or do you plan to do so? Do you think it looks better than the stock icons?
10 Cydia sources to try for the iOS 8.4 jailbreak
The default Cydia repos hold the majority of the awesome jailbreak apps and tweaks that we all know and love, but from time to time, you’ll need to use a third-party source for certain Cydia packages. Some third-party repos, like Ryan Petrich’s beta repo, are one of the first things I add after jailbreaking my iPhone. Other repos aren’t nearly as necessary, but still nice to have available.
In this post, I’ll share with you 10 different third-party Cydia sources that you can add to Cydia to gain access to additional apps, tweaks, and themes. I’ll also showcase one tweak from each repo that makes it worth consideration.
Note that this is a highly curated list, and I’m purposely omitting repos that house pirated tweaks and apps. I also avoid things like myrepospace, as it doesn’t have the best reputation. So while 10 repos isn’t as much as 50 repos, chances are, you’ll find at least one quality release on each repo that I recommend that you’ll derive benefits from.
10 Cydia Repos
- Chewmieser – http://apt.steverolfe.com – StatusVolX/FreeFall
- Elijah and Andrew’s Planet – http://elijahandandrew.com/repo – ReachApp
- HASHBANG Productions – http://cydia.hbang.ws – Pheromone
- Ian’s Repo – http://repo.cydro.us – Cydia Timeout
- Karen’s Pineapple Repo – http://cydia.angelxwind.net – AppSync Unified
- Pw5a29’s Repo – http://pw5a29.github.io – New swipe selection
- Ryan Petrich’s repo : http://rpetri.ch/repo – Tons of stuff, Activator
- tateu’s repo – http://tateu.net/repo – vAlarm
- team Kodi – http://mirrors.kodi.tv/apt/ios – Kodi
- 46&2 Repository – http://repo.fortysixandtwo.com – Wink
Keep in mind that most of the listed repos contain other compelling packages, and most are updated from time to time to upgrade existing packages and add new downloads.
If you’re going to add this many third-party repos, I definitely recommend using CSources2 in order to manage them. This jailbreak tool makes managing repos infinitely easier than going about it solo.
What’s your favorite repo on this list? Are there any repos that you think should definitely be listed here that I omitted? Drop me a line in the comment section and let me know.
Tuesday, July 7, 2015
iOS 8.3 is no longer being signed by Apple
Wishing to downgrade (or upgrade) to iOS 8.3? If so, you’re too late, as Apple just stopped signing iOS 8.3.
As has been the trend lately, Apple tends to continue signing older firmware even after new firmware—such as last week’s iOS 8.4—has been out for a while. This time, a full week passed before Apple closed the doors on iOS 8.3.
What does this mean for users?
It means that if you wish to downgrade from iOS 8.4, you simply can’t. It also means that if you’re on a lower firmware, such as iOS 8.1.3, and wish to upgrade to iOS 8.3 instead of iOS 8.4, you can’t.
In a nutshell, it means that you basically are forced to upgrade to iOS 8.4 in all situations. Granted, there have been some rumblings of potential downgrades, so you should always look into saving your SHSH blobs for all firmwares, but nothing solid has come from this yet.
The good news is that iOS 8.4 can be jailbroken, so it’s not like jailbreakers are out of the game yet. But, this does mean that you should definitely save your iOS 8.4 SHSH blobs in preparation for the next version of iOS that is coming.
As always, you can visit IPSW.me to check the signing status of Apple firmware.
What are your thoughts on this inevitable change?
How to get Apple Watch-styled Lock screen notifications on your iPhone
WatchNotifications is a brand new jailbreak tweak from developer Thomas Finch, that seeks to better unify the look of notifications on Apple Watch and iPhone. It does this by mimicking the look of Apple Watch notifications on your iPhone’s Lock screen.
Available for $1.00 on Cydia’s BigBoss repo, if you prefer the look of the notifications on your Apple Watch, then you’ll most certainly be interested in WatchNotifications.
Once WatchNotifications is installed, it should begin working immediately. The only thing it will affect are the notifications that you receive on your Lock screen, so banners and alerts will still look like they always do on iOS.
But on the Lock screen, Notifications closely mimic those found in watchOS. Functionally, everything is the same—you can still swipe to quick reply, open, and dismiss—but the look is much more in concert with the look found on Apple’s wearable.
In the Settings app, you’ll find a preference panel for WatchNotifications. The preferences for the tweak consist of two switches—a kill switch and an option to disable the app icon shadow the Lock screen notification.
I like WatchNotifications. It’s a good-looking tweak that helps unify the notifications experience, at least from a visual standpoint.
What do you think? Leave a comment down below.
Possible iPhone 6s keynote and launch date revealed
With just two full months to go until the iPhone 6s and 6s Plus are officially unveiled, a Chinese gadget blog has allegedly revealed the launch dates of both the iPhone 6s and 6s Plus — courtesy of sources inside the Foxconn supply chain.
As per Micgadget, Apple’s iPhone 6s keynote is scheduled for Friday, September 11, while the devices will land in stores one week later on Friday, September 18.
The dates (particularly the latter one) makes a certain amount of sense, given that Apple is all but certain to pick a launch day as close as possible to existing iPhone early adopters’ yearly contracts running out. With that said, I’d be surprised if this is any more than a guess, since it seems questionable if Apple would share this kind of information with Foxconn, who Micgadget claims to have heard it from.
As one of our readers points out, it’s also worth noting that last year’s iPhone announcement keynote was on September 9, a Tuesday. If Apple was to unveil the iPhone on a Friday and then make it available for sale one week later, that would mean opening it up for pre-order immediately following the keynote.
Apple is also unlikely to want to hold a keynote on 9/11, although this is likely secondary to the other points.
Either way, I’m excited about the iPhone 6s, which is rumored to be the biggest incremental “s” release in iPhone history. Features are expected to include a RAM upgrade, faster processor, new color option, possible sapphire display for the iPhone 6s Plus, strengthened shell, improved Touch ID, Force Touch, and major camera upgrades both front and back.
Ten weeks to go, provided today’s report is accurate!
'Hacking Team' Data Breach Confirms Firm's Ability to Infiltrate Jailbroken iPhones
Cybersecurity firm Hacking Team experienced a data breach earlier today, resulting in 400 GB of its documents being leaked onto the Internet, reports The Guardian. The documents confirm Hacking Team's ability to infiltrate and monitor jailbroken iPhones on behalf of government law enforcement agencies like the NSA, as noted by Macworld.
Hacking Team uses a legitimate Apple enterprise signing certificate, which is used by corporations to create software that can easily be installed on employee devices, combined with jailbroken iOS devices to bypass iOS app installation protections. Additionally, Hacking Team developed the ability to create a malicious Newsstand app that could capture keystrokes and install monitoring software.
Last year, researchers working independently of each other at Kaspersky Lab and Citizen Lab discovered components of Hacking Team's tools and how they were used by government agencies to steal data from mobile devices, but the full extent of the software hadn't been confirmed until now.
Data breaching software and Apple devices have been in the news before, most famously in last year's celebrity iCloud data breach, where it was discovered that hackers were using ElcomSoft Phone Password Breaker, software intended for government and law agencies, to steal usernames and passwords to access iCloud backups.
While much of the discussion around government agencies and citizen data has revolved around mass collection, Hacking Team's software is designed to attack individual devices rather than a vast network. It's likely that the exploits detailed in Hacking Team's documents will be addressed and patched up in future iOS and Mac software updates.
Note: Due to the political nature of the discussion regarding this topic, the discussion thread is located in our Politics, Religion, Social Issues forum. All forum members and site visitors are welcome to read and follow the thread, but posting is limited to forum members with at least 100 posts.
Much has been speculated before and after Edward Snowden’s release of a trove of National Security Agency (NSA) documents in 2013 about the capabilities of the United States’ agencies as well as those of allies and enemies. The Hacking Team dump reveals quite a bit more about the routine functions of third-party suppliers into that ecosystem, including specifically enumerated capabilities.Hacking Team's software would need to be installed on a jailbroken iPhone, but the firm has the ability to jailbreak and infect a phone with its software via a malware-infected trusted computer the phone is connected to. In the firm's pricing list [PDF, requires Chrome], it's revealed hacking an iOS device costs €50,000 ($55,242) and includes "features" like Skype, WhatsApp and Viber chats, location, contacts and lists of calls. However, this service also includes a prerequisite of a jailbroken iPhone.
iOS users should therefore take note that the long-running concern that jailbroken iPhones and iPads were susceptible to vulnerabilities that could include access by so-called state actors appears to be confirmed by the data breach.
Hacking Team uses a legitimate Apple enterprise signing certificate, which is used by corporations to create software that can easily be installed on employee devices, combined with jailbroken iOS devices to bypass iOS app installation protections. Additionally, Hacking Team developed the ability to create a malicious Newsstand app that could capture keystrokes and install monitoring software.
Last year, researchers working independently of each other at Kaspersky Lab and Citizen Lab discovered components of Hacking Team's tools and how they were used by government agencies to steal data from mobile devices, but the full extent of the software hadn't been confirmed until now.
Data breaching software and Apple devices have been in the news before, most famously in last year's celebrity iCloud data breach, where it was discovered that hackers were using ElcomSoft Phone Password Breaker, software intended for government and law agencies, to steal usernames and passwords to access iCloud backups.
While much of the discussion around government agencies and citizen data has revolved around mass collection, Hacking Team's software is designed to attack individual devices rather than a vast network. It's likely that the exploits detailed in Hacking Team's documents will be addressed and patched up in future iOS and Mac software updates.
Note: Due to the political nature of the discussion regarding this topic, the discussion thread is located in our Politics, Religion, Social Issues forum. All forum members and site visitors are welcome to read and follow the thread, but posting is limited to forum members with at least 100 posts.
How to jailbreak iOS 8.4 with TaiG 2.3.0
TaiG 2.3.0 was just released about an four days ago, and it brings with it support for iOS 8.4. Like previous versions of TaiG’s tool, this version is Windows-only, so you’ll need to use a Windows machine or a virtual Machine.
We’ve created a full video walkthrough and tutorial to show you how to jailbreak your iPhone, iPad, or iPod touch running iOS 8.1.3-iOS 8.4 using TaiG 2.3.0. It’s an extremely easy jailbreak that only takes a few minutes if the directions are followed closely.
Note: this tool requires Windows or a virtual machine running windows. You must have iTunes installed (latest version is fine) for this to work.
Be sure to have Find My iPhone, passcode lock, and location services disabled prior to starting. Enter Airplane mode as well. It’s also best if you use a fresh iOS install, and you reboot before starting. Also, ensure that iTunes can recognize your device before running the TaiG too!
Step 1: Download TaiG 2.3.0 from Her; save and extract it to your desktop
Step 2: Connect your iOS 8.4 device to your computer
Step 3: Launch TaiG 2.3.0
Step 4: Uncheck the 3K assistant checkbox
Step 5: Click Start to begin the jailbreak
Once the jailbreak completes, launch Cydia to start the Cydia initialization process. The great thing about TaiG 2.3.0 and iOS 8.4 is that the current version of Cydia Substrate works out of the box, so there are no weird workarounds or waits to endure until you can use your favorite tweaks. That said, some tweaks will need to be updated and enabled before you can enjoy them.
What do you think? Are you jailbroken on iOS 8.4 yet?
10 Apple Music jailbreak tweaks
Apple Music is here, and I think that we can all agree that it’s a fairly big deal in tech. Now that iOS 8.4 is officially jailbroken, it’s time to look at some of the tweaks available for Apple Music. In the following post, I outline 10 jailbreak tweaks that you may want to try on Apple’s revamped Music app.
Note: Keep in mind that since we just got the iOS 8.4 jailbreak, there may be conflicts when mixing together multiple tweaks.
Also, some of these tweaks still haven’t been officially updated for iOS 8.3 or iOS 8.4, yet they still work very well. Other tweaks may have a bug or two, but are otherwise usable. As the jailbreak matures and more developers update their tweaks, you’ll see increased compatibility across the spectrum. Okay, on to the tweaks!
MusicRotate
This is a new Cydia tweak especially designed for the revamped Apple Music app. It allows users to enable landscape orientation on the iPhone. – Free on Cydia
Fuse
Displays both the Lock screen clock and music controls at the same time. – Free on Cydia
MiniPlayer
Adds an iTunes-inspired mini player to the Lock screen. – $1.99 on Cydia
EqualizerEverywhere
Looking to tailor the sound of a specific type or genre of music? Want more fine-grained control over the music listening experience? EqualizerEverywhere provides you with equalizer presets and lets you adjust various bands to create your own sound. – $3.00 on Cydia
Muswitch
Add music controls above the iOS App Switcher. – Free on Cydia
Spectral
Lends more character to the Lock screen by adding blurred album art as a wallpaper. – Free on Cydia
Aspectus
Adds music controls to the Reachability view. – $0.99 on Cydia
Helius 2
Revamped stylized Lock screen media controls. – $0.99 on Cydia
ColorFlow
Changes the color of the Lock screen and its assets based on the now playing song’s album artwork. Really great when playing a playlist containing various album covers. – $1.99 on Cydia
Flex 2
It’s only been a couple of days, and there are already two dedicated Apple Music Flex patches available. Flex lets you quickly and easily patch different aspects of iOS. Users can create their own patches from scratch, or as the majority enjoy doing, download patches from others. The two Flex patches I used allowed you to hide the recently played section and to hide the dismiss button for the now playing interface. – $3.99 on Cydia
Of course, this is only the very beginning of what’s possible with the right jailbreak tweak. Apple Music, and its feature-set will no doubt open up the doors to more innovation in the coming weeks and months.
What’s your favorite jailbreak tweak for the Apple Music app thus far?
Nella lets you customize the Cydia install interface
Another day, another new Cydia customization tweak. I guess this will continue to be the new trend for the foreseeable future, not that I’m complaining at all.
It’s great to have tweaks that can finally customize Cydia without jumping through a ton of hoops. Nella is the latest such tweak. It lets you customize the colors of the installation interface background and buttons for a truly unique look.
After installing Nella, you’ll need to open up the Settings app and find the preference panel for the tweak. Once there, you’ll see several options for customizing the look of the Cydia install interface.
Options include background color, and text color for the respring button. There’s also the ability to disable the border of the button, and set the border radius.
Lastly, there’s a switch for enabling auto finish. This will cause the device to automatically respring when an install is completed instead of forcing the user to tap the Restart SpringBoard button.
I do wish Nella had some sort of RGB slider or color picker, instead of making users rely on hexadecimal color codes. I also don’t enjoy the fact that any change requires a respring before it will be enacted.
Despite those inconveniences, I still recommend Nella. It’s free, and as you can see from the screenshots above, the end result looks really good.
What do you think?
iPhone 6s is 0.2mm thicker than iPhone 6, leaked industrial design diagram indicates
Apple’s next-generation iPhone 6s should measure 7.1mm deep, a 0.2 millimeter increase versus the current-generation iPhone 6, which measures 6.9mm deep. If true, the 4.7-inch iPhone 6s will have the exact same thickness as the 5.5-inch iPhone 6 Plus, according to a purported schematic leaked Monday to Engadget Japan by a reliable source in the Chinese supply chain.
KGI Securities’ analyst Ming-Chi Kuo previously said that an imperceptible increase in thickness was necessary to accommodate Apple’s implementation of force sensing on the iPhone 6s and iPhone 6s Plus’s screen.
The schematic also suggests a slightly wider and about 0.15mm taller handset versus the existing iPhone 6 generation. The imperceptible change in thickness gives hope that existing cases will be compatible with the new iPhones.
The leaked diagram reveals that the design of the iPhone 6s and iPhone 6s Plus will be barely different than that of Apple’s current iPhones, including the protruding camera lens and the antenna lines on the back.
The next-generation iPhones should offer the same storage options as Apple’s current iPhone lineup. The devices will be reportedly made from a 60 percent stronger Series 7000 aluminum that Apple developed for the Apple Watch Sport.
A supply chain report this weekend claimed that Protek has begun hiring up to 40,000 workers on behalf of Pegatron, which was commissioned alongside Foxconn to assemble the new iPhones, with volume manufacturing expected to ramp up this month.
Bloomberg originally reported that Apple had recently begun early production of the forthcoming iPhone models. The new handsets should go on sale in September.
The iPhone 6s and iPhone 6s Plus are rumored to offer up to twice as fast 4G LTE download speeds via an updated Qualcomm baseband modem, in addition to improved NFC, faster Touch ID fingerprint scanning, a force-sensing screen, a faster and more power efficient, TSMC-built “A9” processor with 2GB of RAM and other perks.
Most importantly, the iPhone 6s and iPhone 6s Plus are said to offer ”the biggest camera jump ever” in the handset’s history with a five-megapixel camera on the front and a twelve-megapixel shooter out the back with 4K video capture and improved low-light photographyvia an extra white sub-pixel alongside the conventional RGB sub-pixels.
A sketchy report by the Chinese blog Feng claims the forthcoming iPhones could come outfitted with a sharper, higher-resolution Retina screen: a Full HD screen on the iPhone 6s model matching the Full HD display of the present-generation 5.5-inch iPhone 6 Plus, with the iPhone 6s Plus reportedly gaining an ultra-sharp 2K Retina screen.
TaiG releases version 2.3.1 beta to include latest Cydia update
In an interesting move, the folks over at TaiG have released a new version of their iOS 8.4 jailbreak tool for Windows, but have labeled it as a beta. Version 2.3.1 beta incorporates the latest version of Cydia, version 1.1.20, and that’s about all.
According to the change log, no other changes were implemented into the TaiG tool outside of the Cydia update. For such a small change, it’s weird that they’ve labeled it as being a beta, but maybe this will become a new trend going forward until they have enough successful testers to deem it a stable release.
TaiG isn’t recommending that users use the beta version, and instead are pointing the public to its most recent public version of the jailbreak tool—version 2.3.0.
Here is what TaiG is saying about the beta tool:
1. V2.3.1 integrates the latest Cydia 1.1.20.2. V2.3.1 is a beta version. If not necessary, you can use the previous version to jailbreak.3. If any problem, please contact us: @TaiG_Jailbreak.
Indeed, it looks as if they’re soliciting feedback from those who use the tool.
Here is the change log for TaiG 2.3.1 beta:
- Integrate the latest Cydia 1.1.20.
You can download TaiG 2.3.1 beta from her.
Does this mean that we’ll begin seeing future TaiG releases, even major one for new firmware builds, come out as beta releases initially? That’s yet to be seen, but with this latest revelation, it’s not out of the realm of possibilities.
What do you think?
Sunday, July 5, 2015
How to Hack Wi Fi Using Android
Two Methods:WPA2 WPS Routers WEP Routers
Do you want to test your network security? It used to be that you needed a desktop OS such as Windows or Linux installed on a computer with a specific wireless network card. Now, however, you can also use certain Android devices to scan and crack wireless networks. These tools are available for free as long as your device is compatible. Hacking routers without permission is illegal. These steps are provided to test the security of your own network and you can find the tools down below at the end of this page
Method 1 of 2: WPA2 WPS Routers
1
Root a compatible device. Not every Android phone or tablet will be able to crack a WPS PIN. The device must have a Broadcom bcm4329 or bcm4330 wireless chipset, and must be rooted. The Cyanogen ROM will provide the best chance of success. Some of the known supported devices include:
- Nexus 7
- Galaxy Ace/S1/S2/S3
- Nexus One
- Desire HD
2
Download and install bcmon. This tool enables Monitor Mode on your Broadcom chipset, which is essential for being able to crack the PIN. The bcmon APK file is available for free from the bcmon page on the Google Code website.
- To install an APK file, you will need to allow installation from unknown sources in your Security menu. Step 2 of this article goes into more detail.
3
Run bcmon. After installing the APK file, run the app. If prompted, install the firmware and tools. Tap the "Enable Monitor Mode" option. If the app crashes, open it and try again. If it fails for a third time, your device is most likely not supported.
- Your device must be rooted in order to run bcmon.
4
5
Launch Reaver. Tap the Reaver for Android icon in your App drawer. After confirming that you are not using it for illegal purposes, Reaver will scan for available access points. Tap the access point you want to crack to continue.
- You may need to verify Monitor Mode before proceeding. If this is the case, bcmon will open again.
- The access point you select must accept WPS authentication. Not all routers support this.
6
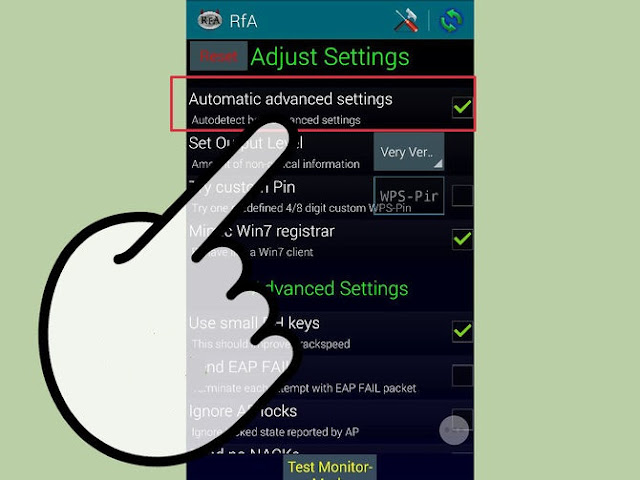
Verify your settings. In most cases you can leave the settings that appear at their default. Make sure that the "Automatic advanced settings" box is checked
7
Start the cracking process. Tap the "Start attack" button at the bottom of the Reaver Settings menu. The monitor will open and you will see the results of the ongoing crack displayed.
- Cracking WPS can take anywhere from 2-10+ hours to complete, and it is not always successful.[1]
Method 2 of 2: WEP Routers
1
Root a compatible device. Not every Android phone or tablet will be able to crack a WPS PIN. The device must have a Broadcom bcm4329 or bcm4330 wireless chipset, and must be rooted. The Cyanogen ROM will provide the best chance of success. Some of the known supported devices include:
- Nexus 7
- Galaxy S1/S2/S3/S4/S5
- Galaxy y
- Nexus One
- Desire HD
- Micromax A67
Download and install bcmon. This tool enables Monitor Mode on your Broadcom chipset, which is essential for being able to crack the PIN. The bcmon APK file is available for free from the bcmon page on the Google Code website.
- To install an APK file, you will need to allow installation from unknown sources in your Security menu. Step 2 of this article goes into more detail.
3
Run bcmon. After installing the APK file, run the app. If prompted, install the firmware and tools. Tap the "Enable Monitor Mode" option. If the app crashes, open it and try again. If it fails for a third time, your device is most likely not supported.
- Your device must be rooted in order to run bcmon.
4
Tap "Run bcmon terminal". This will launch a terminal similar to most Linux terminals.Type airodump-ng and tap the Enter button. AIrdump will load, and you will be taken to the command prompt again. Type airodump-ng wlan0 and tap the Enter button.
5
Identify the access point you want to crack. You will see a list of available access points. You must select am access point that is using WEP encryption.
6
Note the MAC address that appears. This is the MAC address for the router. Make sure that you have the right one if there are multiple routers listed. Jot this MAC address down.
- Also note the Channel that the access point is broadcasting on.
7
Start scanning the channel. You will need to collect information from the access point for several hours before you can attempt to crack the password. Typeairodump-ng -c channel# --bssid MAC address -w output ath0and tap Enter. Airodump will begin scanning. You can leave the device for a while as it scans for information. Be sure to plug it in if you are running low on battery.
- Replace channel# with the channel number the access point is broadcasting on (e.g. 6).
- Replace MAC address with the MAC address of the router (e.g 00:0a:95:9d:68:16)
- Keep scanning until you reach at least 20,000-30,000 packets.
8
Crack the password. Once you have a suitable number of packets, you can start attempting to crack the password . Return to the terminal and type aircrack-ng output*.cap and tap Enter.
9
Note the hexadecimal password when finished. After the cracking process is complete (which could take several hours), the message Key Found! will appear, followed by the key in hexadecimal form. Make sure that "Probability" is 100% or the key will not work.[2]
- When you enter the key, enter it without the ":". For example, if the key was 12:34:56:78:90, you would enter 1234567890.
you can find the tools her
Subscribe to:
Comments
(
Atom
)